Brute Force Detection(BFD) is a critically important part of protecting your server from malicious attacks.
What is a Brute Force Attack?
The most common form of brute force attack is a dictionary attack. A malicious person who is trying to get access to one of your accounts (web server, ftp, e-mail, ssh, etc.) uses a file containing dictionary words to attempt rapid logins. The dictionary file contains a list of usernames and/or passwords, and a script or program uses the dictionary file to attempt rapid-fire logins against your server using one or more of the services mentioned above.
How does BFD Work?
All of the various services on your server maintain log files including logs that note failed login attempts. BFD works by watching these various log files for failed login attempts and if it detects several of them in a short period of time from the same source IP address (the person attempting to connect to the server) it will block that IP address in the server’s firewall.
To summarize: BFD stops people from guessing your passwords with massive dictionary lists and then prevents them from connecting to the server at all by blocking their current IP address in your server’s firewall.
BFD for Linux Servers
If your Linux server is running cPanel then BFD is already installed. You can view or modify the BFD settings by logging in to your WHM and finding the navigation link to the left called Security Center, pictured below:
On the Security Center page click on the link called cPHulk Brute Force Detection, pictured below:
An example of the cPHulk BFD configuration screen:
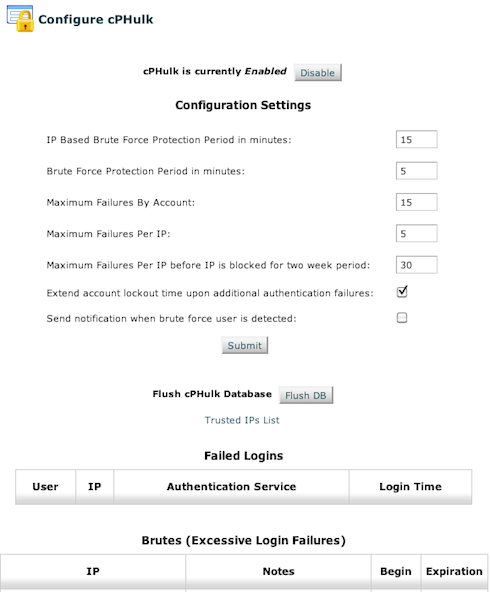
The default settings shown above are in use by the vast majority of cPanel servers as of when this content was posted. If you have questions regarding changing these settings please open a new support request using the contact information listed at the bottom of this article.
If you have an IP address that you want cPHulk to always ignore (such as your home, office, etc) you can click the Trusted IPs List link.
I got blocked from my own server by BFD! Now what?
In most cases once you have been blocked by your server’s BFD system or Firewall, the easiest way to regain access is to unblock your IP Address in the AlpineWeb Customer Backroom. For instructions see the following Knowledgebase Article:
https://www.alpineweb.com/backroom/knowledgebase/71/How-to-unblock-your-IP-address.html
The vast majority of cases that our support department handles involving customers who are blocked by their own servers are due to FTP clients that contain a saved password. If someone in your company, group, organization, or household changes the password to that FTP account and doesn’t notify you to update your saved password it is quite easy to end up blocked by the server. Most FTP clients automatically reconnect several times if the initial attempt fails, and once your FTP client with the bad password attempts to login several times and fails the server’s BFD system will kick in and block your IP address.
Customers in an office environment that utilize a private network connected to the internet may find their entire office blocked by their server. This happens (usually in a small/home office situation) when multiple computers are sharing a single internet connection, meaning they also share the same public facing IP address. Once a single computer on that local network gets blocked by the server all of the other local computers will find themselves blocked as well.
While this can cause some initial panic there is no need for concern. Even if you are temporarily blocked by your own server that does not mean it is down. It may be ignoring your requests for a short while but it is still working away, handling the tasks from other visitors to your web site(s).

