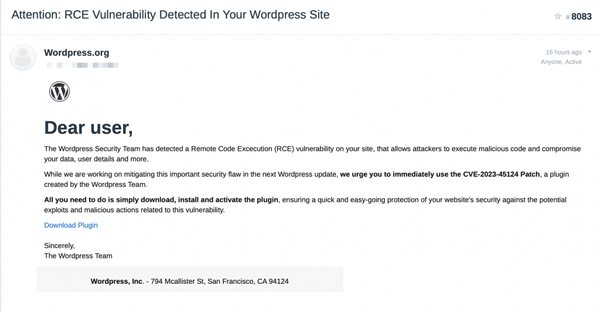
For the past couple of days, we have been monitoring a mass-scale phishing campaign with multiple variants of phishing emails going around that are notifying users about a supposed security vulnerability in their WordPress website.
IMPORTANT: Vulnerability detected - Your website yourdomain.com is at risk!
The Remote Code Execution (RCE) vulnerability detected on your site is categorized as a critical threat, potentially enabling malicious code execution and putting your data, user informations, and overall site security at risk.
We urge you to use the CVE-2024-46188 Patch as soon as possible, while we are working on fixing this crucial security concern in the upcoming WordPress update.
Simply download the plugin by clicking the button below, install and activate it on your site. This guarantees swift and seamless defense against potential exploits and malicious actions linked to this vulnerability.
With a Download Now button.
This is not a legitimate email and the plugin that they are asking you to download and install will infect your website with a backdoor and malicious administrator account.
This means that this campaign has no impact on you as long as you do not download and install their malicious plugin! WordPress would never ask you to install a patch like this. Instead, they would publish a new version of WordPress core as a security release.